Imagine for a moment that Alice, a hacker, was looking at various means for receiving payment for an illicit activity she just undertook. She has two options to do so, which would she choose?
(1) Bob built a payment network which was identity-free; it used pseudonyms so no legal identities were required to send transactions between its participants. And that trying to stop or prevent payments was difficult because the computers running the payment network were widely distributed and run by multiple known and unknown participants across dozens of jurisdictions that were sometimes hard to track down. Recourse is difficult and sometimes impossible. Cryptocurrencies such as Bitcoin, Litecoin, and Ethereum are examples of such a network.
(2) Carol built a payment network which requires all users to provide a proof-of-identity, usually by scanning and storing of government-issued IDs or utility bills. And that stopping, preventing, or even rolling back payments was possible because the computers running the payment network were run by legally identifiable participants who were often located in easy-to-find offices. Recourse could be cumbersome, but almost always possible. Wire transfer methods like ACH are examples of such a network.
Alice would probably choose number one and later try use some conversion tool or exchange to move her payment into number two. How is this done? See the (dated) flow-of-funds chart below.
While some cryptocurrencies, like Bitcoin, were probably not designed to serve as get-away vehicles – because of key design choices that make legal recourse difficult – they are increasingly used to shuffle ill-gotten gains around.1
For example, data kidnapping – commonly referred to as ransomware – has existed in some form for more than two decades. But the current plight surrounding ransomware, and the white washing of the role cryptocurrencies have in this plight, have gone hand in hand over the past several years.
Why?
The core characteristics of cryptocurrencies – censorship resistance and pseudonymity – are some of the main reasons why ransomware has become increasingly commonplace. And these cryptocurrencies need liquidity.
Liquidity into-and-out of fiat has fluctuated over time, with some exchanges being debanked and sometimes rebanked, but as an aggregate it has increased overall. Liquidity is often done through venture-backed gateways and exchanges.
As explored in my previous post, as well as others, many of these gateways and platforms have inadequate and typically non-existent KYC and AML gathering processes. This post won’t go into the details surrounding some of the investors and promoters of these platforms, but further research could dive deeper into that industry as well as the white washing that goes on to distract investigations.
We see this empirically: attackers do not ask for fiat or credit cards because these would be easily tracked and/or transactions would be halted. Instead, they ask to be paid in some kind of cryptocurrency because they know the likelihood of getting caught and reprimanded is significantly lower.
This past Friday, WannaCry, a ransomware package, wreaked havoc on more than 200,000 victims across all times of organizations located in over 150 countries. This included government services including NHS in the UK and the Interior Ministry in Russia.
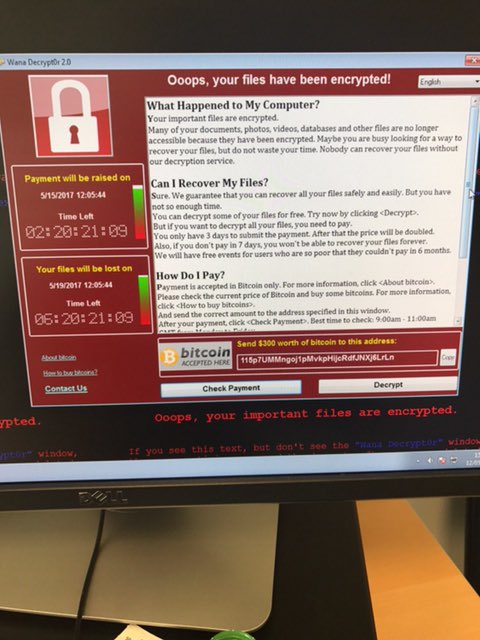
Source: Twitter
The first-order of victims ranged from small startups that could quickly patch and restart their computers all the way to large hospital systems that were unable to access patient records and had to turn away patients.
This then leads to the second-order of victims: patients and customers of these institutions. According to the Associated Press, the “cyberattack hit almost 20 percent of UK’s 248 public health trusts.”
A consequence of the ransomware outbreak, a patient says, 'My heart surgery was cancelled’ https://t.co/Omw1dZqjRu
— Jeremiah Grossman (@jeremiahg) May 12, 2017
“Bitcoin ransomware” hit CN univ. Student theses locked, while BTC wd not allowed. Some may face delay of graduationhttps://t.co/91frl3qk7y pic.twitter.com/wTq5bFxYNj
— cnLedger (@cnLedger) May 13, 2017
While all of the impacted organizations already should have had a formal plan to upgrade and patch these types of vulnerabilities (e.g., create regular back-ups off-site), based on several news stories, many of them did not.
Will they all learn from this lesson? Probably not.
Either way: none of the victims have a formal means of recourse against the hacker(s) involved in WannaCry because we do not know the identities of the hackers. Some victims have even paid the ransom of ~$300, denominated in bitcoin, to have their files unlocked. The hacker is using multiple (4+) bitcoin addresses to receive the ransom and as of this writing, has received more than $50,000. 2
Last year the FBI estimated that around $1 billion was paid to unlock ransomware and cyber extortion. Cryptocurrencies, such as Bitcoin, were usually the preferred method of payment.
Two weeks ago, James Comey, former Director of FBI spoke before the Senate Judiciary Committee and noted that:
Some of our criminal investigators face the challenge of identifying online pedophiles who hide their crimes and identities behind layers of anonymizing technologies, or drug traffickers who use virtual currencies to obscure their transactions.
For Bitcoin, there are ways to remain fairly anonymous, like using mixers, however it requires a lot more work to. But relatively few people are investigating, so the chance of getting caught is likely low. Newer cryptocurrencies such as Monero and Zcash are designed to be anonymous which makes them harder to track. Monero has been spotted in the wild alongside the Kirk Ransomware as well as research from Sophos (pdf).3 And Zcash has been used by a botnet to mine more Zcash on devices such as your phone.
And then there is Tor, a software program that enables anonymous communication by passing network traffic through various relays nodes that help conceal the location of the user. WannaCry used Tor to preserve its “anonymity by proxying their traffic through the Tor network.”
How to bring some light into the darkness?
Solutions
I reached out to Adam Young who co-created “cryptoviral extortion” (what we call ransomware today). In his view:4
In terms of the ransomware attack, people/organizations need to do a better job at patching and removing end-of-life systems, clearly. My larger concern is that cryptoviral extortion is the only cryptovirology attack that anyone seems to be paying attention to and there are many, many others.
I also spoke to Danny Yang, CEO of Blockseer who advised everyone to, “update your software, make sure you have latest security patches – that ransomware worked because people didn’t update their Windows since March when that particular security vulnerability was patched.”5
My recent post looking at Bitfinex and regtech was quite popular. It was viewed several thousand times and I received a number of calls from reporters looking to investigate some of the points raised.
Some people pointed out that the behavior by Bitfinex and other cryptocurrency exchanges is one of the reasons why a few banks in emerging markets have lost correspondent banking access: that they were de-risked because of what others perceive is a high-risk customer base.
According to research by Accuity, a global financial crime compliance, payments and KYC solutions provider:
Between 2009 and 2016, correspondent banking relationships, where one financial institution provides services on behalf of another in a different location to facilitate cross-border payments, have reduced globally by 25%.
Earlier this year, the People’s Bank of China, SAFE and other government bodies in China, investigated and froze cryptocurrency withdrawals at many, if not all, the cryptocurrency exchanges operating on the mainland.
Why? Among other reasons: inadequate KYC and AML gathering and sharing processes.
According to Caixin, a notice of administrative punishment may be released in June that details the punishment and fines of these China-based exchange operators.
In addition to freezing and de-banking, what are some other solutions as well?
Companies such as Blockseer and Chainalysis provide tools for law enforcement, regulators, entrepreneurs and compliance teams to trace and track the flow-of-funds on cryptocurrency networks. I have written about them numerous times.
Angel List is tracking 96 startups involved in providing compliance-related software for SMB, hospitals, cloud providers, social media platforms and a handful of other verticals. It also has job listings for 11 regulatory compliance startups. There is an additional 2,878 startups listed under the broader category of big data analytics, some of whom who are also working in the regtech space.
While technology can help play a role in identifying participants on these types of networks (blockchains and distributed ledgers), it is also worth exploring the proposed strawman for setting up a Kimberley Process for cryptocurrencies. Identity systems are critical to all property rights and financial networks. Creating applications around data lineage, data provenance, KYC management, and standardized digital identities will help provide transparency into all markets.
If you’re interested in learning more about these tools and mechanisms, feel free to reach out or leave a comment below.
Endnotes
Share the post "How cryptocurrencies enable ransomware and how regtech can help counter it"
- In the original white paper, Nakamoto explained ways to route around trusted third parties, such as governments. [↩]
- If you’re interested in learning more about how malware researchers identified and stopped it, Malware Tech has a detailed story as well as one from Brian Krebs. [↩]
- AlphaBay, the largest darknet market by volume, announced that it was accepting Monero as a form of payment in August 2016. [↩]
- Private correspondence, May 14, 2017. Published with his permission. [↩]
- Private conversation reused with permission. May 13, 2017 [↩]


Great, in-depth analysis of cryptocurrency, thanks.
May I ask, in a world where a private key held on a hard drive, or in a pocket, can constitute money, and bits sent over the Internet can constitute a payment from one entity to another, might KYC on all this work?
It’s my understanding that hackers can demand payment in any one of several hundred different cryptocurrencies, if KYC is enforced (and by whom; as has been seen with the persistence of torrent sites – it’s like a global game of whack-a-mole, across 170+ jurisdictions)…
I think as Adam Young and Danny Yang proposed, organizations are going to need to patch their servers. And it would certainly do us all a lot of good if the CIA hadn’t kept these exploits secret, after President Obama publically promised Microsoft and others [1] that the NSA will disclose any exploits they are aware of in software being relied upon by customers of those American technology companies. Unfortunately, we now know the CIA simply picked up where the NSA had left off. I don’t suppose Trump has made any fresh assurances, so we can safely assume that further exploits exist, and may one day wreak fresh havoc. Best to keep those servers patched!
Incidentally, they made $50,000, is that all? I suppose then, the best tactic with ransomware is to simply not encourage them by paying.
[1] https://www.wired.com/2014/04/obama-zero-day/
Great post. Blockchain technology is one of the most important inventions of all time, but it creates a whole new host of possible issues. Now hackers can simply hack into your computer and steal thousands of dollars worth or more of Cryptocurrencies and then tumble them to make them untraceable. It’s a real issue.